Today’s data center focused and organized Internet services are just like dinosaurs – they were very successful at their time, but eventually vanished in a continuously changing world. If services shall be successful in the future, they have to take data sovereignty of their users/consumers into account. Being decentrally organized, local operation (in personalized devices such as smart-phones, smart home servers, PC and others we currently do not even dream of), anonymity, and resilience are their immanent characteristics.
"Do Not Put All Your Eggs into One Basket"...
...an ancient proverb, which is fully applicable to Digital Sovereignty. If we want to become sovereign of our data again, we have to replace the currently predominant approach based on centrally managed data and the accumulation of a person’s information items in one place.
Facebook with its personalized profiles and Amazon with its buying recommendations show how NOT to play the game in the future. A personalized screen shows the data which users have classified as relevant for themselves (which are originating from third parties, be it friends, colleagues, family, and others). The users typically do not know which other personal information beyond that accessible to them is managed by the social network.
What are the advantages of such a centralized approach? First and foremost, it provides relevant, personal data for the operators of social networks (or virtual shopping malls and other data accumulators), which can be transformed into income (very often through advertisement or thorugh direct sales pitches). It is this business model, which most new, consumer oriented Internet services depend upon. Cross references to similarly minded users can be easily calculated (if not provoked), expected user behavior can be forecasted quickly. Or how should someone ordering a pregnancy test device get adverts for diapers 9 months later?
What are the advantages for the consumer of a service on the Internet? Of course, if I am interested, I can profit from the forecasted recommendations (e.g. of books which I could be interested in). But maybe I do not want anyone else to know about my pregnancy? Then the centralized approach has mostly disadvantages.
„Divide et Impera”
Do I have a choice? Of course, by local operation and decentral management of the relevant data.
Let us take a little excursion back in IT-History: despite their introduction only in the 1960’s, IT systems have already undergone a number of architectural revolutions. In the early years a small number of central mainframe systems were thought to be sufficient for most purposes. However, with the introduction of (smaller) office computers in the 70’s and eventually with the widespread adoption of the Personal Computer (PC) in the course of the 80’s, the de-central, personal approach had complemented or replaced the central data processing systems. Corporations were still using mainframes, but PC users’ data were stored locally and only when necessary were made available to others via slow telecommunications lines. Also, many information items were only available in analogous form (for example music or films). This decentral architecture changed again around the turn of the century with the spread of the Internet, the adoption of mobile telephony, and the increase of transmission speeds of fixed and mobile networks. Suddenly there was a business case for new service providers, which used the faster networks to collect data centrally and redistribute them to interested users, often at no visible cost from a user perspective. Google, Amazon, Facebook built a number of giant data centers, which lead us back to the times of the mainframes. The smart-phone in this scenario is used as a relatively “dumb” appendix of the networked data centers. It is used to collect user data (as sensors are a major component in modern smart-phones). Users access their data in the network through smart-phones.
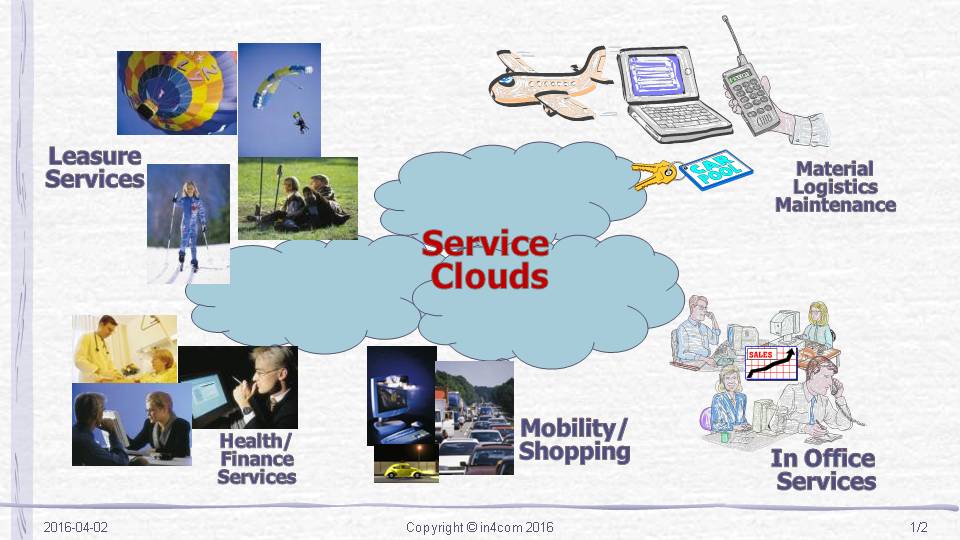
The computational power and storage capacity of a modern day smart-phone go far beyond a 70’s mainframe’s. Why should a smart-phone not be capable to perform the required, personal calculations locally which are currently done at a data center? And at the same time integrate information from data centers which collect data from other service users or service providers (at no cost or with a price tag). Then my data would not need to leave the smart-phone – or only in anonymized form. This would get us back to be the sovereign of our data. We would be able to decide if at all, which data, under which conditions, and to whom we would make our data available.
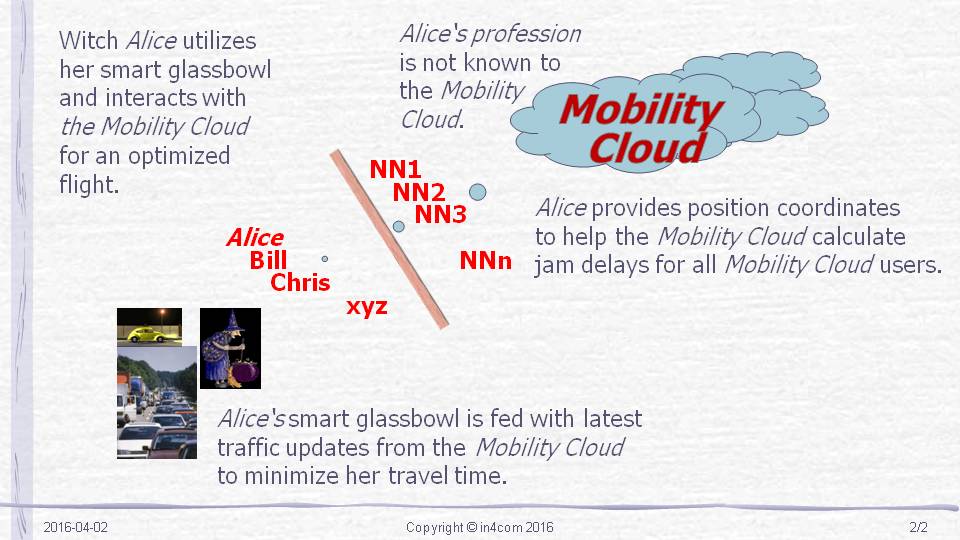
As already indicated, anonymity is a foundational principle of all proposed data exchanges between individual users and data centers in the network. There is no reason why a traveller’s identity must be available for the optimization of traffic flows on a motor way or in a city. Pseudonymity (i.e. anonymity in a weaker form which allows a later recalculation of an individual) is only required in a small number of situations and could be handled by (semi) official agencies for increased trust. For the authorization of transferred data, certification entities for the data could be used which do not jeopardize the expected anonymity (we have already indicated new business opportunites following this model). The generation and later transmission of data can be done securely with the help of crypto mechanisms.
Last but not least, we have to mention another foundational architecture element of a future secure Internet economy: resilience. As of today, we must expect errors and faults which can lead to failure of the distributed, decentralized services – a number of statistics and research in software shows this clearly. Therefore, it is assumed that safe and secure programs expect failures to occur und envisage corresponding resilient behavior. Network availability will never be 100%, core software based systems can only achieve a nearly 100% availability, but not 100%. Therefore, software in a data center or in a personal device, which is used to implement important or even critical functions (e.g. power generation, navigation, heart-rate monitoring) , should be checked for resilience in case of failures (and only be allowed to enter production mode after certification).
Read more on secure services and data sovereignty
- Security as differentiator
Data Protection THE Business Driver for New Apps and Services
Digital Transformation is Based on Data Sovereignty - Security Architectures
Architectures for Secure Internet Services (this report)
Object orientation (work ongoing) - Security Technologies
in preparation - Regulierung und Datenschutz
in preparation - Data Sovereignty
Digital Sovereignty - What is it?
Digital Sovereignty – why we need it
Data Sovereignty - Why Do We Give It Up?

